select the best answer. which of the following are breach prevention best practices
A single technology cannot provide complete protection. Which of the following are breach prevention best practices.

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
There are Microsoft best practices best practices and practices.
. PCs cell phones PDAs and the network says Pappas. Select the best answer. Access only the minimum amount of PHIpersonally identifiable information PII necessary B.
Closed Claim Case Study. All of the above When must a breach be reported. Best Practices for Enterprise Cloud Security.
Change the DNS servers in the list to. Over the last 10 years pfSense software has amassed a following and installed base of nearly 400000. 8 hours agoEnsure 100 breach prevention and manage your entire security estate with a unified policy from a single point across networks clouds Mobile Endpoint and workloads.
Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security. 13 Best Practices You Should Implement. Should be the only source for product performance data.
True Select the best answer. Contain the data breach to prevent any further compromise of personal information. Access only the minimum amount of PHIpersonally identifiable information PII necessary B.
Mobile Device Policies for Preventing HIPAA Data Breaches. In my case I will be. All of the above.
Access only the minimum amount of PHIpersonally identifiable information PII necessary. If you deal with private data regularly encryption is vital. Answer Which of the following are breach prevention best practices.
Select the best answer. Which of the following are breach prevention best practices All of the above. What is the best.
HIPAA Data Breaches and PHI on Stolen Laptops. Now with the GDPR in full effect we will likely see these costs increase. Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion.
S3 Breach Prevention. Employee Voyeurism Leads to a HIPAA Data Breach. When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information.
Promptly retrieve documents containing PHIPHI from the printer D. Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very difficult task. This paper focuses solely on the aspects of re-establishing best practices safety.
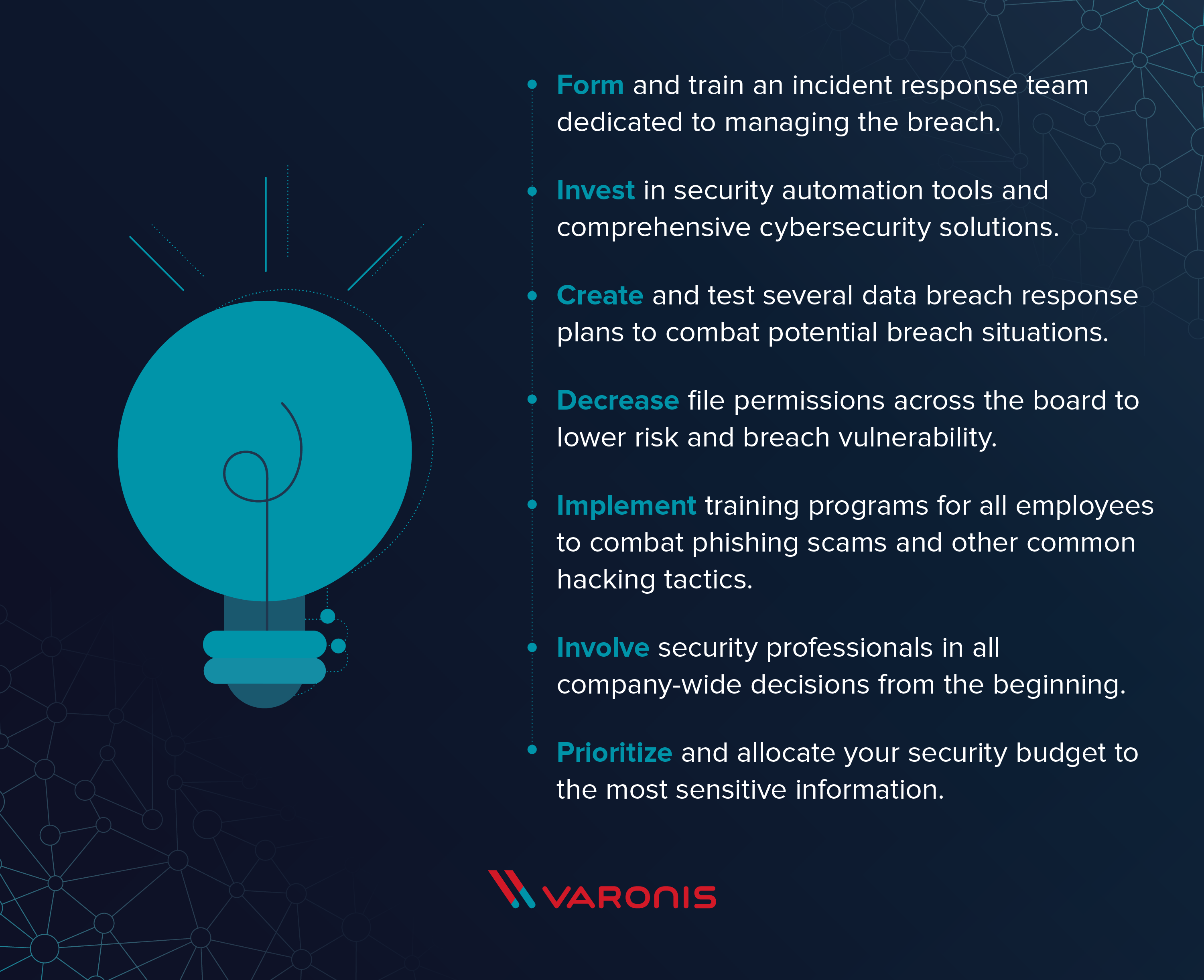
Other terms for this phenomenon include unintentional information disclosure data leak information leakage and also data spillincidents range from. Assess the data breach by gathering the facts and evaluating the risks including potential harm to affected individuals and where possible taking action to remediate any risk of harm. The following are breach prevention best practices.
In the United States the average total cost of a data breach stands at 819 million more than twice the global average. Closed Claim Case Study. Select the best answer.
Which of the following are common causes of breaches. Created By Madyson Hartmann. 20 Which of the following are breach prevention best practices.
It describes a process and its elements for. Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Promptly retrieve documents containing PHIPHI from the printer.
Conduct a Risk Assessment Before any solution is implemented it is important to know. When gathering data about product performance one should keep in mind that customer complaints. What are breach prevention best practices.
They need to be secure at the host eg. Logoff or lock your workstation when it is unattended C. None of the above 4 Sample Exam Questions 12.
Logoff or lock your workstation when it is unattended. Are a poor measure of product. Which of the following are HIPAA categories for punishing violations of federal health care laws.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 1 Under HIPAA a covered entity CE is defined as. He recommends campuses have firewalls. Share this link with a friend.
Misdelivered Email Results in a HIPAA Data Breach. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. Breach prevention best practices for the prevention of.
For example sort data into groups such as confidential data general data internal data and external data and maybe even assign each with a distinct color then train employees to follow this system. Notify individuals and the Commissioner if required. Which of the following are categories for punishing violations of federal health care laws.
Provide reliable performance data.

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Data Loss Prevention What Is Dlp How Does It Work

Analyzing Company Reputation After A Data Breach

What Is An Incident Response Plan And How To Create One

Data Loss Prevention Best Practices Endpoint Protector

What Is Data Security Definition Planning Policy And Best Practices Toolbox It Security

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

10 Business Ethics Online Courses Edapp Microlearning Programs

Kubernetes Best Practices 8 Tips To Improve Security Cycode

Unauthorized Access 5 Best Practices To Avoid Data Breaches

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
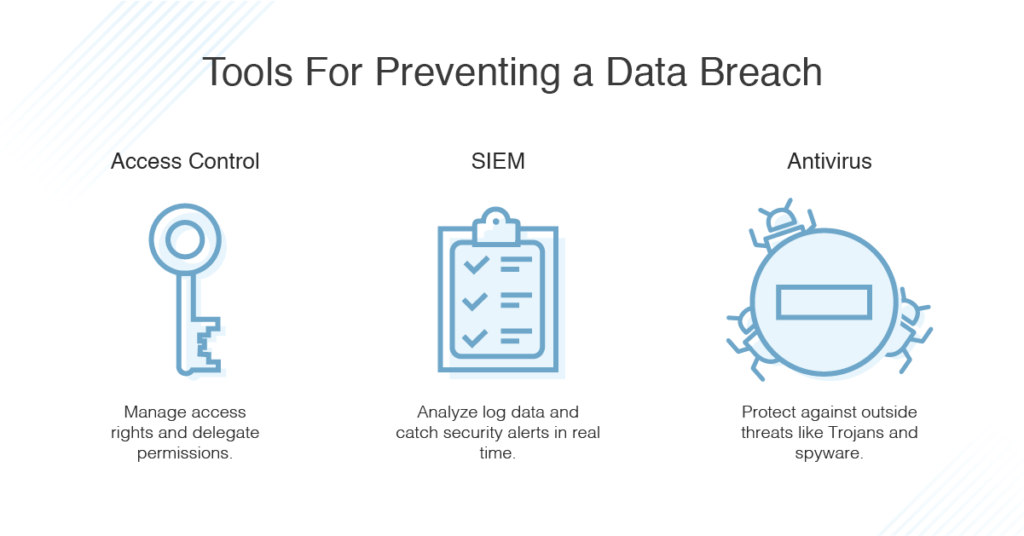
What Is A Data Breach Definition Types Dnsstuff

The 5 Best Employee Monitoring Software Of 2022 Vendor Comparisons

The Ultimate Data Breach Response Plan Securityscorecard

Data Breach Response Times Trends And Tips

Pdf Mobile Security Threats And Best Practices
Frequently Asked Questions About Data Loss Prevention Endpoint Protector